Nmap 5.00 is the latest and greatest version of what is arguably the most useful network utility ever created and it's now available, for all major computer operating systems, from the download page at nmap.org. Nmap is Free and Open Source Software.
The previous stable release of Nmap was version 4.76 way back in September 2008 and much has happened since then - this version of Nmap is packed with new features and numerous improvements. You can read the official details of this release at http://nmap.org/5/.
So what is Nmap exactly? How about a little introduction:
Nmap Port Scanning
Nmap, the port scanner, is able to discover services running on a networked host by utilising a variety of scanning techniques and probes in order to help you gather important information about the function of the host and the state of the network.
Try this command against scanme.nmap.org (a host provided, as the name suggests, for testing your favourite port scanner):
$ nmap scanme.nmap.org
Nmap's abilities make it easy to troubleshoot problems on the network, enforce network policies, test firewall rules and much more. Nmap is a must-have tool for Network Professionals, System Administrators, Security Professionals and just about anyone who uses a computer in a networked environment and who wants to know more about their network environment or just networking in general.
Read more about Nmap Port Scanning techniques at http://nmap.org/book/man-port-scanning-techniques.html.
Host Discovery
Nmap excels at finding hosts on the network: your network; someone else's network or even the entire Internet. Nmap is able to send a great variety of probes for many network protocols in order to elicit responses from hosts, thus revealing their presence.
Try running a command such as one of the following to find hosts on your local network:
$ nmap -sP --reason 10.0.0.0/16
$ nmap -sP --reason 192.168.1.0/24
The following will generate 1024 random IP addresses and report any hosts it finds out there on the Internet:
$ nmap -sP --reason -iR 1024
Read more about Nmap and Host Discovery at http://nmap.org/book/man-host-discovery.html.
Nmap Version Detection
Discovering that port 80 is open on a host means that it's a fairly safe bet that the service available via that port is a web server of some kind - port 80 is the standard port for the HTTP protocol. Nmap can tell you exactly which kind of web server down to the product name and it's version number.
Try this command against port 80 of scanme.nmap.org:
$ nmap -sV -p80 scanme.nmap.org
Version detection has been a part of the Nmap arsenal for several years and is one of its greatest strengths. The Nmap database of service detection probes and probe responses allows Nmap to identify thousands of services even when those services are running on non-standard ports. No longer is it a good idea to hide services by binding them to non-standard ports (e.g. hiding telnet on some high numbered port such as 50000 instead of its standard port 23) and assuming that the service won't be found. Nmap will quickly reveal the service's true identity!
Read more about Nmap Version Detection at http://nmap.org/book/man-version-detection.html
Nmap Operating System Detection
Another great feature of Nmap is its ability to detect small differences in the way a host speaks over the network in order to identify the Operating System (OS) running on the host. Under ideal conditions Nmap is able to accurately detect more than 2000 different versions of OS from Apple iPhones to ZyXEL ZyWALL routers and including standard ones such as Ubuntu or Windows Vista and obscure ones running on devices such as Oscilloscopes and Toasters (OK, not really toasters - not yet anyway...).
Try this command against scanme.nmap.org to discover what Operating System it runs:
$ nmap -sV -O scanme.nmap.org
Read more about Nmap Operating System Detection at http://nmap.org/book/man-os-detection.html.
Nmap Scripting Engine
The Nmap Scripting Engine (NSE) allows its users to write custom scripts in the Lua scripting language to perform any kind of networking task imaginable. NSE provides access to Nmap's networking APIs and makes it very easy to send and receive data across the network. Nmap ships with over 50 scripts which complement and extend the discovery of information about a host - tasks such as detecting open proxy services, detecting open mail relays, looking-up Autonomous System Numbers and WHOIS information, detecting and exploiting vulnerabilities and many more.
Try the following command against the web service at scanme.nmap.org to discover the Title of the default web page:
$ nmap -p80 --script html-title scanme.nmap.org
There are also more than 30 NSE libraries to allow script-writers to easily implement all sorts of common networking tasks such as sending HTTP requests and parsing the responses, performing DNS queries, talking the SMB protocol to Microsoft Windows machines to name but a few. The Lua language is easily mastered and its use within NSE is well documented making it very simple to start writing NSE scripts.
Read more about the Nmap Scripting Engine at http://nmap.org/book/man-nse.html.
Nmap and Accompanying Tools
Nmap has become a suite of tools for Network discovery, exploration and management and as well as the main Nmap executable, Nmap 5.0 now comes with the Zenmap GUI, Ndiff and Ncat:
Nmap and the Zenmap Graphical User Interface
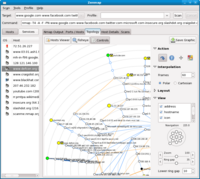
Zenmap is a cross-platform graphical user interface for Nmap with several really
cool tricks up its sleeves. The killer features of Zenmap include a graphical
view of the network Topology and its ability to Aggregate the results of
multiple scans into a single place. Using the results of Nmap traceroute output
(option: --traceroute) Zenmap draws an actual map of the network which includes
the routers between you and the target host. Result Aggregation allows you to
perform multiple scans and Zenmap extends the map to include any new hosts
discovered. Information about any host is available for viewing right there on
the map making it a great way to build-up a picture of hosts on the network.
The map is displayed as a series of concentric circles each representing a 'hop' with your host at the centre, but the map can be redrawn with any host at the centre allowing you to view the network from different perspectives. The map can even be exported as an image for viewing outside of the Zenmap interface.
For people new to Nmap, the Profile Editor is a fantastic way to learn about and experiment with the huge array of Nmap options. The Profile Editor explains each of the options and presents them in an easy to use interface which allows you to select options by ticking boxes, selecting items in drop-downs and so on. Zenmap profiles are a great way to save Nmap commands which you use regularly and Zenmap ships with several ready-made profiles to get you started.
Command line junkies need not use the Zenmap Profile Editor at all - commands can be typed directly into the Zenmap Interface and using Nmap this way is just as quick as from the command line with all of the added benefits that Aggregation and Topology bring. Zenmap also produces both the normal output associated with a command terminal as well as Nmap XML output which means you don't have to worry about specifying Nmap output options - Zenmap allows you to simply save the output to a file once a scan is finished and you can even save multiple scans to a single directory in a couple of mouse clicks.
Zenmap has other features too such as: maintaining a database of recent scans so that you can search them to find specific hosts or services you're interested in; enabling comparisons between the results of two scans to quickly see the differences in the output; and novel ways to display information about scanned hosts.
Read more about Zenmap at http://nmap.org/book/zenmap.html and marvel at just how useful it is.
Ndiff and Nmap Output comparisons
Nmap can produce its output in XML format and a common desire is to compare the output of two scans of the same host or network taken at different times. Ndiff is a separate command line tool, shipped alongside Nmap, which allows you to quickly see the differences between the outputs of two scans in a similar way that Unix diff works. Ndiff is Nmap aware and excels at showing you changes in available hosts on the network and changes in port states of a host - making it really useful for keeping abreast of changes on the network. Zenmap leverages Ndiff for its scan comparison functionality.
Read more about Ndiff at http://nmap.org/ndiff/.
Ncat - Netcat for the 21st Century
Ncat is a modern re-implementation of Netcat and is fundamentally a tool for reading from and writing to the network. Ncat has a nearly limitless number of uses like acting as a simple TCP, UDP or SSL client to a variety of network services, providing network functionality to non-networked applications, acting as a server to which clients can connect and cool things like becoming a proxy server, a chat client/server and the brokering of connections between clients. It features security measures such as access control lists for client connections and proxy authentication.
Like the rest of the Nmap toolset, Ncat runs on all major operating systems and has no trouble communicating with an Ncat running on a different operating system.
Read more about Ncat at http://nmap.org/ncat/.
Nmap Network Scanning - Fyodor's Nmap book
Nmap's author Fyodor has also authored Nmap Network Scanning - the "Official Nmap Project Guide to Network Discovery and Security Scanning". The book is a 468 page treasure trove of information about how to effectively harness the power of Nmap in the real world including a 42 page reference of all Nmap options. The book is available for purchase and several of its chapters are available in the free online-edition at http://nmap.org/book/toc.html
This has been a short introduction to Nmap 5.00 and its associated tools which I hope you've found useful. If you want to know more about Nmap, you will find everything you need to know at http://nmap.org/.
Happy Nmapping!